Victim loses $11 million to permit phishing
Sportsbet.io likely hacked for $3.5 million
SportsBet has not yet disclosed any theft.
- Telegram message from zachxbt [archive]
"Read-only" CoinStats crypto application enables wallet breaches
The application asks its users to connect their wallets to allow it to track their holdings, but promises on the website that it offers "the ultimate security for your digital assets". "Since we ask for read-only access only, your holdings are perfectly safe under any conditions," the website promises, later touting its "military-grade encryption".
CoinStats shut down the platform while investigating the incident. Losses have been estimated at around $2.2 million.
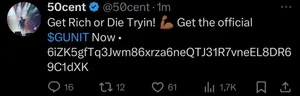
50 Cent claims his accounts were compromised to promote a memecoin
50 Cent also claimed in the post that "Who ever did this made $300,000,000 in 30 minutes." It's not clear where 50 Cent got this number, because the token has only done $19.8 million in volume. One wallet made around $722,000 off the token, and three others also made over $100,000.
- Instagram post by 50 Cent
- $GUNIT on DEXScreener
BtcTurk exploited for at least $55 million
It appears that assets notionally worth around $55 million were stolen. Furthermore, the exploiter sold substantial amounts of some cryptocurrencies, including Luna Classic, causing major price movements in those tokens.
According to newly installed Binance CEO Richard Teng, Binance froze $5.3 million of the stolen assets.
- BtcTurk status page (in Turkish) [archive]
- Tweet by Richard Teng [archive]
CertiK and Kraken accuse each other of misconduct over bug report and $3 million "testing"
However, others have noted that the number of transactions and amount of cryptocurrency taken by CertiK while "investigating" the bug seems to far exceed the norm for whitehat security researchers, and that they took cryptocurrency amounting to millions of dollars — making their "testing" look a lot more like a blackhat theft. Furthermore, CertiK made several transfers to Tornado Cash as part of their "testing" — an entity that is sanctioned by the United States.
Kraken alleged that CertiK did not disclose the full extent of their employees' transactions, and refused to return the $3 million they had taken. They also alleged that CertiK had attempted to extort them. Kraken said they had been in contact with law enforcement, and were "treating this as a criminal case".
Ultimately, CertiK returned the funds. However, it's not clear if criminal action may be ongoing.
Martin Shkreli claims to have been behind a Donald Trump memecoin
Shkreli attempted to frontrun the news in a Twitter space, and came out with his own claims that he had collaborated with Barron Trump to create the token, and with Andrew Tate to pump its price. However, fellow felon and memecoin pumper Roger Stone subsequently crawled out of the woodwork to claim that neither Barron nor Donald Trump was involved with $DJT.
Shkreli has yet to provide solid proof that he created the memecoin, though zachxbt's research tends to be very strong. If true, Shkreli faces potential legal repercussions, as he is still on parole after his release in 2022. The terms of his parole require him to "refrain from engaging in self-employment which involves access to client's assets, investments, or money, or solicitation of assets, investments, or money", and to make financial disclosures to the courts. Shkreli was also banned from the securities industry in 2018, as part of a settlement with the SEC.
Holograph exploited for more than $1.2 million
One of the addresses involved in the exploit appears to have contributed to the Holograph protocol, though it's not clear if they took advantage of insider knowledge to pull off the heist.
- "HLG Down Over 60% as Exploiter Mints 1 Billion New Tokens", CoinDesk [archive]
- "Holograph fell 80% in 9 hours after exploiter mints 1B additional HLG", Cointelegraph [archive]
- Etherscan data for one of the attacker's wallets [archive]
UwU Lend re-enables protocol after hack, immediately gets hacked again
UwU Lend was created by Michael Patryn, aka Omar Dhanani, aka "0xSifu", who has been behind several cryptocurrency projects that have suffered major exploits. This is not exactly helping concerns among some observers that perhaps Sifu is the common denominator in these suspicious losses.
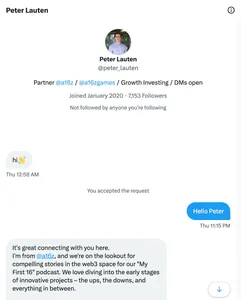
Phishing scammers impersonate Andreessen Horowitz employee to drain crypto wallets
@peter_lauten to @lauten, and snapped up the previous username. They then began contacting various targets in the cryptocurrency world, asking to set up meetings to arrange appearances on the venture capital firm's crypto podcast.The scammers followed a familiar playbook in which they asked their targets to download video call software called "Vortax", which was actually wallet draining malware. However, these scammers had a leg up on some others who have been running that scheme: the Andreessen Horowitz website still listed Lauten's old username on their website, giving even skeptical victims some reassurance that the account was legitimate.
According to crypto sleuth zachxbt, who first reported on this incident, one victim lost $245,000 when his wallets were drained by the malware.